# Netfilter framework
Netfilter is a framework provided by the Linux kernel that allows various networking-related operations to be implemented in the form of customized handlers. Netfilter offers various functions and operations for packet filtering, network address translation, and, port translation, which provide the functionality required for directing packets through a network and prohibiting packets from reaching sensitive locations within a network.
iptables and nftables are build on top of this framework
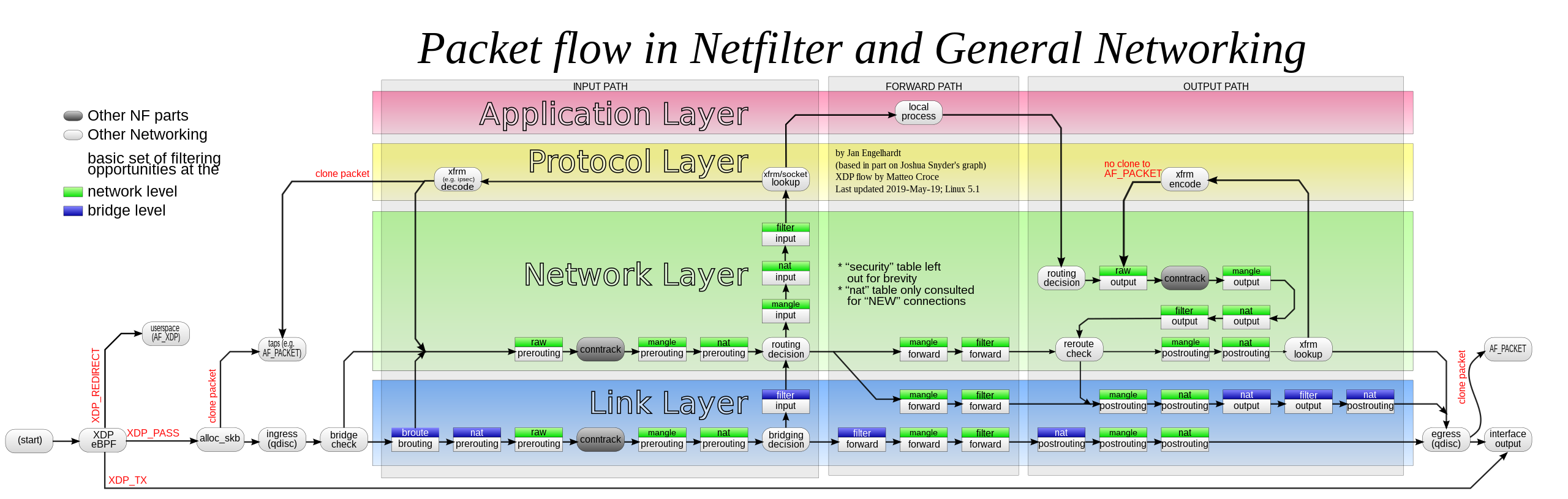
# Netfilter hooks & hook functions
# 5 hooks
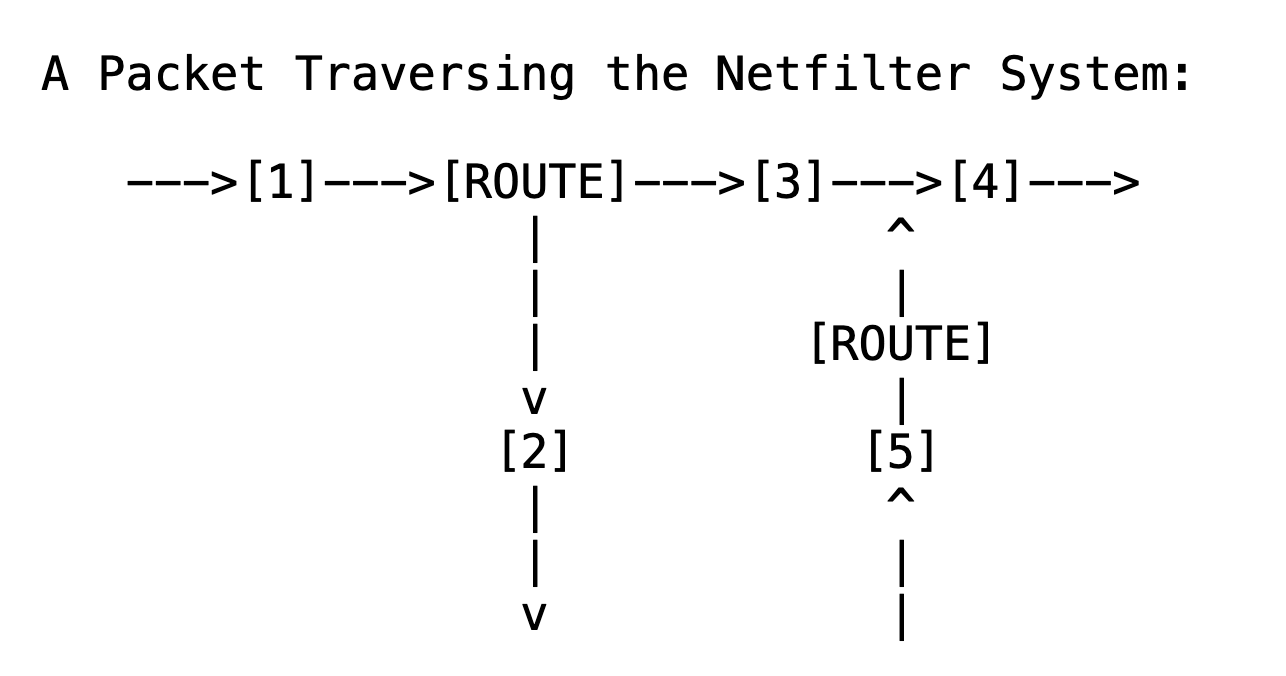
Use IPv4 as an example, when packets pass sanity check (i.e., not truncated, IP checksum OK, not a promiscuous receive), packets are passed to [1]PRE_ROUTING hook
The ROUTING decides whether the packet is destined for another interface, or a local process
If packets are delivered to local, it will go through [2]LOCAL_IN hook, then sent to local process. For locally created packets, it will go through [5]LOCAL_OUT hook
If packets are delivered to another interface, it falls into [3]FORWARD hook
Before packets being put on wire, it need to go through [4]POST_ROUTING hook
# hook functions
Functions with priority can be register with one hook. When Packet goes through a hook, hook functions will be called in the order of priority, then packet can be ACCEPT, DROP, STOLEN, QUEUE, or REPEAT
# iptables
iptables has been the preferred packet filtering and processing system in the Linux kernel since the release of Linux kernel 2.4 in 2001. The rules are organized by iptables into tables and chains, and packets traverse different tables and chains in order.
NAT: does NAT on packets. Only the first packet in a stream will hit this table. After this, the rest of the packets will automatically have the same action taken on them as the first packet. The objectives are DNAT, SNAT, MASQUERADE, and REDIRECT.FILTER: firewall; take actions against packets and look at what they contain and DROP or /ACCEPT themRAW: set a mark on packets that they should not be handled by the connection tracking systemMANGLE: alter IP headers of packets, such as TOS, TTL. But these targets can only be used within MANGLE tableSECURITY:
Here describes the chains of each table based on fig1
| Table | Chains |
|---|---|
| NAT | PREROUTING, INPUT, POSTROUTING, OUTPUT |
| FILTER | INPUT, FORWARD, OUTPUT |
| RAW | PREROUTING, OUTPUT |
| MANGLE | PREROUTING, INPUT, FORWARD, POSTROUTING, OUTPUT |
| SECURITY | * |
# nftables
nftables is the successor of iptables to address problems with iptables. (it’s also the successor of ip6tables, arptables, ebtables, and ipset). The development on ipatbles has been stopped, and the nftables is the replacement. New features and performance improvements primarily go into nftables.
For operations, Red Hat provides a manual for its product: Getting started with nftables
# k8s with iptables, nftables & IPVS
Kube-proxy is iptables based proxy that proxies L4 traffic to service, and then to the Pods. There is enhancement proposal to switch kube-proxy from iptables to nftables:KEP-3866
The motivations for doing this is
- iptables is the performance bottleneck (size of ruleset; overhead of making changes; etc)
- upstream support (nftables > ipatables in Linux kernel)
- etc
IPVS is built on netfilter framework as well. It’s part of the Linux kernel which supports L4 load balancing
kube-proxy also supports IPVS mode, and kube-router is built on top of IPVS
I stop here as I have another post that discussing IPVS and kuber-router in detail
